Examples from the Inventory View More →
The Ultimate Retaliation: Pranking My Roommate With Targeted Facebook Ads
With only $1.70, his roommate’s Facebook user name, and some careful daily-life observations, Brian Swichkhow’s revenge prank on his roommate triggered real concern about a leak in his personal information. Brian was able to create Facebook ads using his roommate’s private details and target them specifically to his roommate. The highly personal ads created an illusion for his roommate that he was under watch. Throughout the prank, Brian remained anonymous by selecting personal details known only by his roommate’s close friends. The news of the Edward Snowden controversy further convinced his roommate that he was under watch. Although Brian revealed himself in the end, and his roommate’s life was restored to peace, the target marketing technology the article presents is still very unsettling. Audience targeting
Read moreZoological and the meaning of movement
Can autonomous, algorithmically driven objects be “sensitive”? What about “entrancing,” or “menacing”? Some certainly seem to think so after visiting the exhibition Zoological, created by Random International for an immersive installation called +/- Human as part of the 2017 Bloomberg Summer season at the Roundhouse Theater in London. When visitors walked into this installation, they were met with eight delicate, autonomous orbs hovering above them in the air, moving algorithmically in response to one another and to other movements in their environment. This might include lazily gliding around one another, or coming to swarm directly over a viewers’ head. The Guardian’s review of the installation was so taken by the spooky sensations evoked by the orbs as to emphatically declare that “the true secret of
Read moreAddressing Network Anxieties with Alternative Design Metaphors
The vision of the smart home that hosts human lives in its embrace with technological intelligence has been part of the cultural imagination for decades, if not longer. As network technology evolves, it has brought not only the smart home, but a high level of connectivity to all aspects of our lives. Now that our long-idealized future is arriving, what wrinkles might appear in its lustrous fabric when seen up close? Some problems have already begun to arise in recent years, such as the surveillance and privacy concerns related to the Google Home and Amazon Alexa systems. In this inquiry, Pierce and DiSalvo cast a wide net to consider network technology in terms of human anxiety. Their speculative approach imagines not so much the difficulties,
Read moreeGregor
eGregor is a research project by Christine Geeng about better aligning common mental models for smart personal assistants (SPA) with the reality of how they function. Geeng seeks to use imagery drawn from the Cthulhu Mythos, wherein humanity encounters grotesque beings so complex and vast that they are utterly incomprehensible, to provide users with a more complete understanding of how their SPA actually works. SPAs are household assistants that have functions such as setting timers, reminders, making phone calls, all based on voice commands from the user. Popular models include Amazon’s Alexa and Apple’s Siri. The legal documents describing the use and storage of user’s data for these devices are often hard to access and even harder to understand. As a result, the mental model
Read moreNetworking with Ghosts in the Machine: Speaking to the Internet of Things
The phrase Ghost in the Machine was created by philosopher Gilbert Ryle in 1949 and acts as a metaphor for the separation of mind and body. As an extension of this dualism, Lindley, Coulton, and Alter conduct a series of experiments that try to bring forth the digital “ghosts” that exist within physical networked machines (Internet of Things). The research described in the article is speculative and exploratory as the authors try to uncover novel design heuristics. They hope to help researchers, practitioners, and students conceptualize and better understand the socio-technical complexities of IoT. This exploration is important given the rapid rise in IoT and humans’ changing relationship with these physical-but-digital networks. The authors’ approach to Spooky Tech is through the framework of Post Anthropocentric
Read moreGhosts!
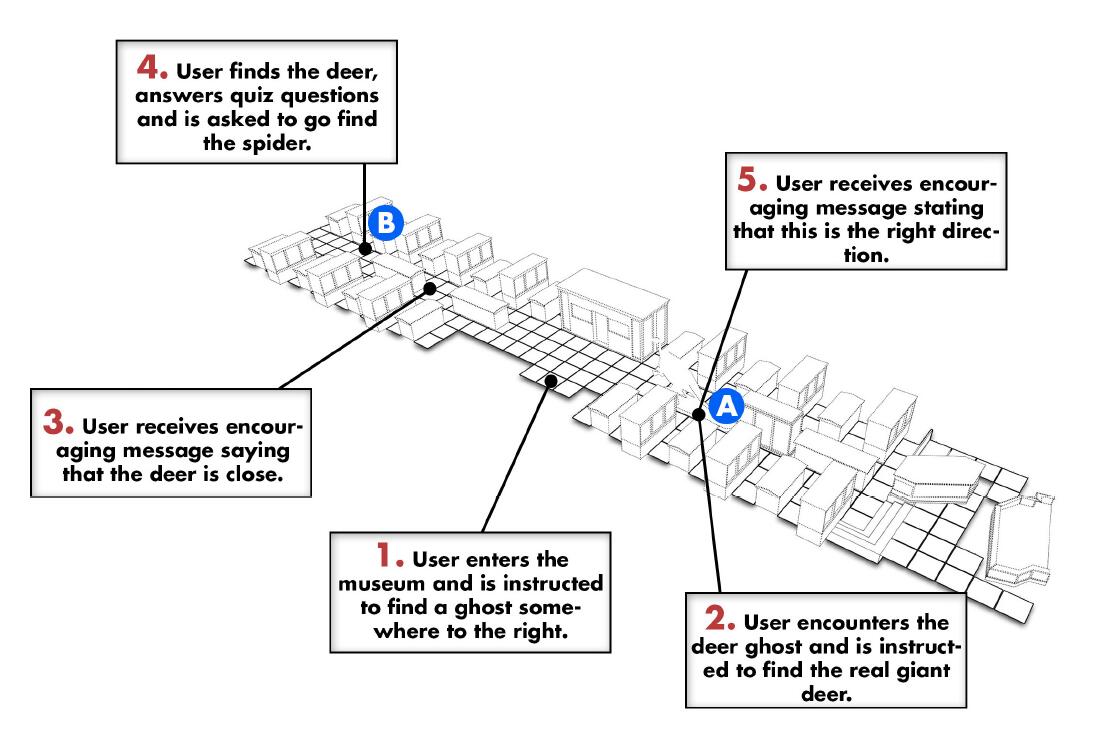
Ghosts! is a location-based Bluetooth Low Energy Mobile Game. When the user walks around the museum with Ghosts, they will encounter ‘ghosts’ on the screen, saying that they are lost and need the visitors’ help to find their home artefacts. The artefact is equipped with its own BLE beacon, which is sent out periodically for the device to detect. When walking through the museum space, the visitors will be informed whether their direction is correct or not, based on the received signal strength of the beacon. If the signal is blocked, the ghost will require the visitor to walk into a more open space or raise the smartphone to redirect. By carefully selecting the artefacts for each ghost, the developer can also guide the visitors
Read more